Microsoft has banned some Azure Cloud applications from its cloud that the company identified as part of an attack infrastructure. Microsoft describes the approach taken by the attackers, a group that is called Gadolinium.
Microsoft describes the cyber group that has preferred to attack companies from the health sector for almost a decade. Recently, Gadolinium has expanded its attacks to include higher education and local government.
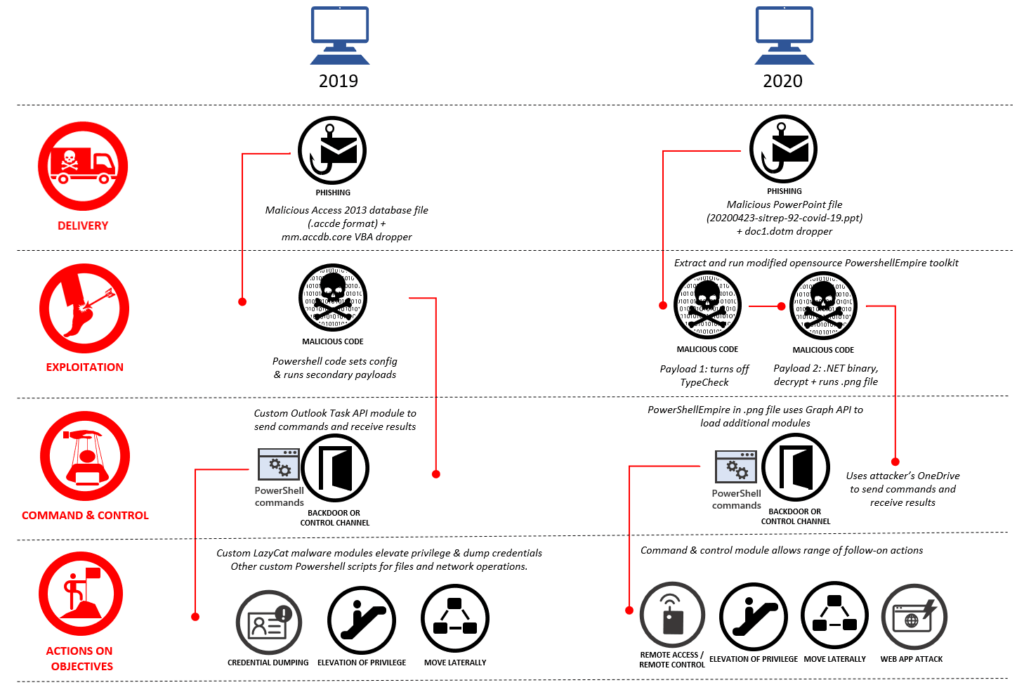
The attacks began with spear emails that were to malicious files attached, mostly on the subject of the pandemic, according to Microsoft’s analysis. Recipients who opened the emails were infected with the based malware. Their job was to configure the victims computer so that they could copy information to their own storage.
Gadolinium Increased Using Open Sources
Over time, Microsoft observed how the hacker group refined its attacks. While the group used to rely on proprietary malware, which can be identified easily by the software, it is now increasingly using open sources such as Microsoft’s command line interpreter, with which attacks are much more difficult to identify. As soon as this malware was successfully installed on the victims computers, it could reload additional modules as required.
The attackers also learned how to use the infrastructure over time. Cloud services offer the advantage that you can use them for free. This means that they are set up quickly; another computer does not have to be laboriously infiltrated for the main computer. Because no access was hacked to use these offers, the servers appear legitimate at first glance. Microsoft finally identified the servers that were used for the attacks.
Microsoft repeatedly takes action against cyber criminals who allegedly take action out of China. The company is also involved in the fight against hackers from Russia and North Korea.
