Bitdefender security researchers have discovered a new type of highly advanced spyware program targeting Android users; the purpose of which is financially motivated and distributed through the Google Apps Market. Researchers called the threat “Mandrake,” and it is estimated that there may be hundreds of thousands of victims during the entire four-year period.
Malware on Google Play
Operators of Mandrake released seven malicious apps on the Google Play market, including “Abfix, CoinCast, SnapTune Vid, XE Currency Converter, Office Scanner, Horoskope, and Car News” to build trust in users.
To claim the status of a legitimate app, these apps have dedicated microsites, Facebook pages, social media accounts like Twitter, Telegram or Reddit, and even YouTube channels, and all of them are harnessed to attract the interest and trust of users.
The researchers emphasized: “In addition to posing as legitimate applications, these applications use additional technology to bypass Google Play protection; they significantly delay malicious activity and operate in stages.
Three steps: dropper, charger, and core. These functions have different roles and complexity.
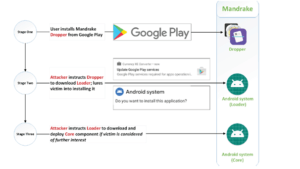
Threat infrastructure
Mandrake uses multiple encrypted command and control servers, as described below; most of which have been active for a full four years. The researchers discovered an active androidfirmwaretop C2 server associated with the IP address “159.69.66.184” and hosted by “Hetzner Online GmbH” in Germany.
| Domain | Registration Date |
| rendfiles.top | 11-02-2016 |
| androidfrimware.com | 06-04-2016 |
| android-soft.top | 09-04-2016 |
| androidfirmware.ca | 06-06-2016 |
| nfmmlrkagflemt.top | 17-11-2016 |
| xjkbhysexthnpl.top | 23-11-2016 |
| livingstream.mobi | 14-12-2016 |
| androidfirmware.top | 21-08-2019 |
Known C2 Servers
Malicious applications hosted by Google are primarily targeted at banking applications such as CommBank, NAB Mobile Banking, Westpac Mobile Banking, Bankwest, Bendigo Bank, St. George MobileBanking, ING Australia Banking, Australian Super, Beyond Bank Australia.
Other destination apps fall into the cryptocurrency, communications, gaming apps, and product categories.
For example PayPal mobile money: fast shipping and request for funds; Microsoft Outlook: email and calendar organization; Google Pay: use of mobile phones to pay and send cash; quick search in Amazon Shopping; convenient viewing of transactions; best shopping on AliExpress; a Better life, Coinbase: buy and sell Bitcoin, encrypted wallet, Bitcoin blockchain wallet, Bitcoin Cash, Ethereum, and VIP access.
The campaign has mastered all the elements of a professional espionage platform, and this attack is likely to be financially motivated.
This threat can easily override two-factor verification codes submitted by some banks to prevent fraud.
Perform phishing attacks on the target application by loading web pages and pasting specially crafted JavaScript code; to extract all the data from the input form loaded in the overlay web component.
In some cases, for a legitimate application, which is itself a web view, the user does not know that it is interacting with the credential theft page.
As a backup measure in case JavaScript injection fails, there is a screen recording, this MP4 recording is saved as <timestamp>.dat in the private files dir and sent later to the C2 server with a post request to URL http://androidfirmware.top:8888/?r=<victim UID>.
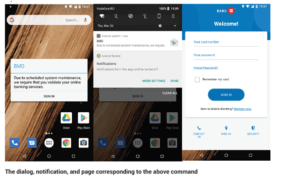
Phishing attack – An overlay screen
