A recent finding has shown that about 15 billion passwords and usernames are distributed on the dark web. This compromise will bring about credential exposure. ATO abbreviation for Account takeover is a malicious activity that hackers take over real user’s account online
Safeguarding our sensitive online information depends on having passwords for our personal information, financial documents, and other confidential files. Hackers don’t only target financial accounts or ecommerce accounts but all types of online accounts, including websites for adults, streaming and cable TV subscription sites, and VPNs sites.
Stolen credentials pegs at 15 billion
Going by the report of “From exposure to Takeover,” published by the digital shadows photo team of researchers. About 15 billion credentials for sale in the dark web draw a 300% increase in stolen credentials from 2 years ago. These stolen credentials are taken from about 100,000 discrete breaches, and 5 billion of these 15 billion credentials are authentic.
These compromise range from a simple account to a whole organization account. They are auctioned or on sale for as low as $3,139 and as high as $140,000. Domain administration access ads with descriptions like big university, a petrochemical company, Petroleum Company, Cybersecurity Company, and different state governments are on sale.
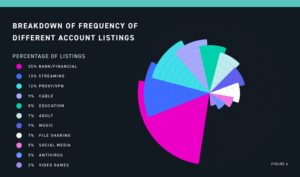
The tools for threats discovered.
One of the attacking tools for sale at hacker forums that cost $4 is the Brute-force cracking tools. Some ads on display are bland like the USA bank login cracker Bruter. Still, other ads are explicit, and it indicates targeting a specific service such as Spotify, Minecraft, and Hulu. Other ads that are on display are Zeus and warbot botnets, Burp suite professional application, sentry MBA account cracker.
Openbullet, a newly created tool, is used for customized configurations and help lower CPU usage.
It comes with multiple tools that aids in parsing data, scraping, unit testing, automated penetration testing via selenium.
The most sectors with breached credentials are below:
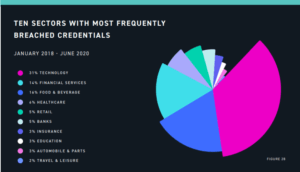
The technology credential is 31%, food and beverage is 16% while financial services are 14%. The monitoring network activity should be adopted to monitor the leaked credentials of the customers.
