This article is about how to use open-source intelligence(OSINT) to discover a person’s virtual footprint and collect personal data. Therefore, OSINT is described in the simplest way by which we can collect information from publicly available resources. These sources are not limited to online searches or Google.
Steps to perform OSINT
First, you should start with information you know, such as email address, username, etc.
- First, you need to start with what information you know, i.e., email, username, etc.
- Then you will define your requirements.
- Now start gathering the data by using OSINT Tools.
- After collecting data start analyzing it.
- Validate your assumptions.
- At last, generate the report
Based on these steps, let’s look at what information we can collect about known components and what resources are available on the Internet for this purpose.
Username Search – OSINT
Suppose I have a target username and need to collect as much information as possible from open sources. The following flowchart shows how to access the data associated with a username from a single username.
You can access the email address of the target username, since many times the username is obtained from the email address. If this is not the case, you can specify the address and find it under “I have been pwned”.
You can also collect millions of data simply by entering your username in a search engine, and you can access your social network account.
How to Perform OSINT on Email Address
Suppose I have a destination email address, and the following flowchart shows how to use this message to display the personal data associated with it.
The first thing to do is to verify the email address you have. For this purpose, there are some online tools available which are described below:
1. Proofy
Proofy is a powerful email verification tool that allows you to do more than 96% accurate email verification.
-
Email permutator
This tool will generate tons of valid email addresses when you enter the name and domain of a person you seek.
-
Hunter
lets you find email addresses in seconds. You just have to type a domain name to launch the search. The Domain Search will list all the people working in a company with their names and email addresses found on the web.
4. OSINT browser extension
The browser extension has many useful links, including links to search and check email. They are compatible with Firefox and Chrome.
After confirming the email address, you can delete your domain to obtain a username and access your social network account. You can also search for the email address directly on social media like Facebook, where the employer will be listed, possibly your real name or other relevant information.
OSINT Investigation using Phone Numbers
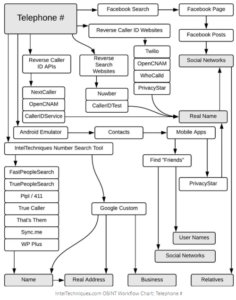
Users of social media accounts (such as Facebook) often associate phone numbers with their Facebook profiles. Even in a Facebook search, you can find your personal number if the privacy level is moderate.
Additionally, user-supplied phone number databases (such as truecaller.com or whocalledme.com) can collect millions of data by selling their services for results.
There is a very famous PhoneInfoga tool that can scan phone numbers using only public resources.
Domain name OSINT
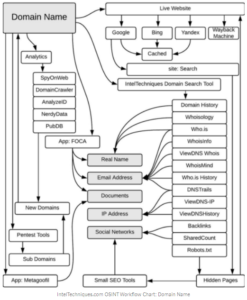
If you know a website of a person owns that you are investigating, then it will quickly reveal important information related to it, such as the operating system being used, software version, personal contact info, and more. Many utilities can perform this job for you:
- Whois
- Reverse whois
The Top 3 OSINT Tools
Many automation tools are designed for this purpose and can simplify the task of solving more complex problems. If your query is intended only to find relevant information about the data, you can use the options above.
For complex OSINT investigation, the following tools are convenient to get the on-demand results.
- TheHarvester
- Recon-ng
- Maltego
Maltego
This is open-source software developed by Paterva. The tool solves more complex problems by processing some of the information as part of the information and then finding links to additional data associated with it.
Recon-ng
Recon-ng is a command-line intelligence tool whose interface is similar to Metasploit. As you begin your exploration, you will be in a shell-like environment where you can configure parameters, perform acknowledgments, and display results in various types of reports.
TheHarvester
A simple and handy tool will fetch the right information of the target. It is useful for scanning domains and gathering information like emails, subdomains, hosts, employee names, open ports, and banners from different public sources like search engines, PGP key servers, and SHODAN computer database. It also uses some common social media platforms like Yahoo, LinkedIn, Facebook, etc.
Conclusion
This article is about how a person collects information through open sources. Even a non-technical specialist with zero knowledge of network security can use online resources to collect a large amount of published data on the terrestrial network with just a few clicks.
