The new trojan Ghimob tries to lure victims into installing the malware documents stating that they are in debt. The documents contain a link that supposedly leads to further data. As soon as the trojan is installed, it sends a message to the server about the successful hack. This contains data about the phone, whether it has a lock screen and installed applications that could be hacked.
Ghimob Can Spy On 153 Different Apps
These apps are mainly from companies and stock exchanges. Ghimob is a spy that his victim carries around with him all the time. The hackers can remotely access the device and carry out fraudulent information. By using the victim’s phone, they can avoid institutions and their networks from recognizing them, identifying them and taking security measures. Even if the user uses a lock screen pattern, Ghimob is able to install and play it to unlock the device.
When conducting a transaction, the hackers could display a screen overlay or open some pages. The malware is carried out in the background while the users are looking at their screen. Finance programs that are already open or logged in and that are installed on the device are used.
The desire of the cyber attackers for a banking malware with worldwide reach has a long history. Security researchers have already identified some hacker groups, who were heavily geared towards the Brazilian companies. In fact, Ghimob is the first mobile trojan in Brazil ready for global expansion. Experts think this new campaign can be linked to the threat for a well known banking malware. This is particularly indicated by the use of the same infrastructure.
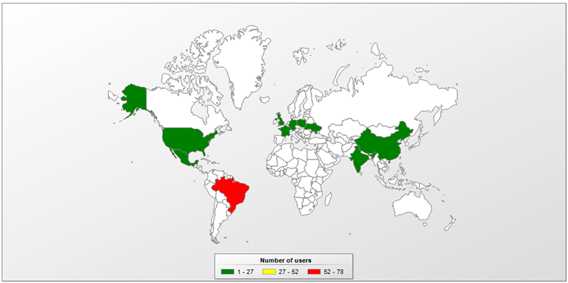
To protect devices from such malicious threats, an endpoint with device features should be used. This ensures that only trusted applications from an approved whitelist can be installed on the devices that have access to company information.
