Users of the Italian National Institute for Social Security (INPS) are the recent victims of a phishing campaign. CERT-AGID presented the findings of D3Lab in their published security advisory. These findings contained detailed information about the technique used by these actors to carry out their fraudulent activities.
The threat actors have implemented a new strategy meant to strip Italians of indemnity from the Government. The payment already promised by the Government shared with citizens who meet certain requirements.
The criminals are taking advantage of the method of payment, which is via the IPNS; by introducing a malicious APK named acrobatreader.apk, a Trojan-Banker malware.
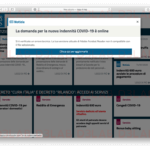
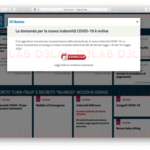
A post published by D3Lab reads, “our research and analysis center for Phishing campaigns detected in the past few hours a new Phishing campaign against INPS users, similar to the previous one of April 6 2020. A web domain created Ad Hoc with similarities in the name to the official one of the national social security institution; used to carry out the fraudulent activity with the intent to download malware to users interested in receiving the Covid-19 allowance allocated from the Italian state.”
The pattern of attack is quite similar to previous ones. In that, the threat actors set-up false INPS sites to lure victims into downloading malicious apps. Unsuspecting citizens visit the website to download the supposed app for the new Covid-19 indemnity but redirected to the malware.
The malware searches for accessibility service to exploit the valid functions of the service; gains access to communicate with other apps on the device through the system’s API.
“As soon as the presence of connectivity is detected, an HTTP POST request is sent to C2 through the following url ” http: // greedyduck [.] Top / gate [.] Php ” passing two parameters:
” Action “: with botcheck or injcheck values ;
” Data “: information collected and passed in encrypted form (RC4).”
The CERT-AGID published the Indicators of Compromise (IoCs) here.