The pandemic has turned out to be a gift for cyber attackers. For some time now, the KashmirBlack hacker group has been driving up the number of ransom incidents in many countries worldwide. The hackers come neither from the USA and also from Indonesia. Experts have now gathered enough evidence to uncover and stop botnet attacks.
Malware And Exploit Vulnerabilities
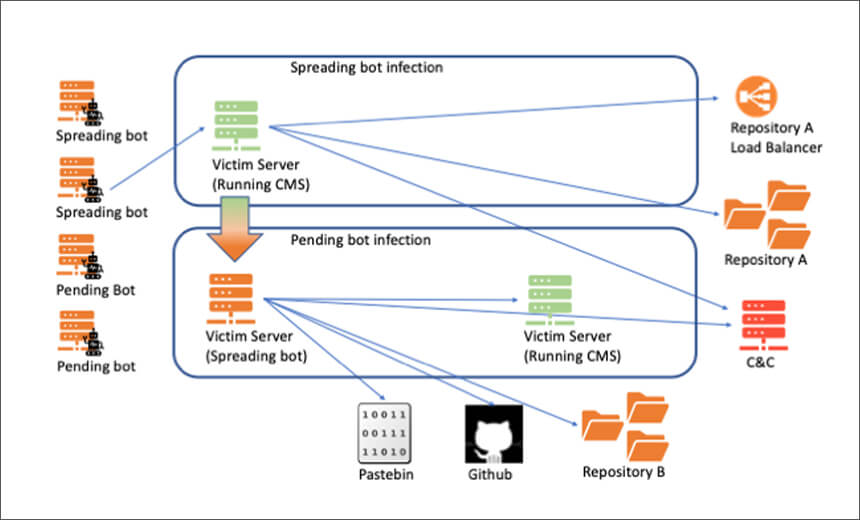
KashmirBlack uses CMS platforms such as entry points to install malware on third party devices – and to expand its system. At this moment, the group infects a lot of servers every day in many countries around the world. In order to spread its malware and smuggle them into the networks, the malware uses the latest advances in software development. This describes an approach that, in the case of KashmirBlack, continuously uses the dangerous malware while they are spreading so that they remain undetected.
Servers At The Center Of The Attacks
However, the malware programs are not new attacks. What makes the malware unique is how they communicate with each other and with the control server. From here they call up their malicious data, receive new instructions and can be continuously modified. The experts were able to identify some components of the network; each individual has an important role to play. What the system tools have in common, is a shared goal: to smuggle malicious scripts onto third party and take control.
Cyber experts reveal that neither the malware nor the attack is new – it is just how the cyber attack is structured and managed that makes the malware so unique. In order for the hackers to receive the malicious code from their headquarters and in turn to be able to play back, they need additional storage. At first glance, these repositories are online platforms, but they have been hacked. The more the group grows, the more storage space it needs.
