Since the corona related move to the home office, the number of daily hacker attacks on remote desktop connections has increased more than tenfold. In June 2020, security manufacturers recorded up to 3.5 million RDP attacks within one day on the lifeline between companies and remote employees.
Companies Underestimate The Risk
Obviously, many companies do not take the threat posed by RDP seriously or cannot find any other solution. The explicitly deals with the question of securing connections between companies and home offices. 30 percent of the companies in Europe stated that their employees only need a password to verify their server login. Not even half of the companies let their employees access with a secure connection. Only 30 percent use two factor authentication for secure access.
The results clearly show that there is still a lot of catching up to do when it comes to securing the network. In most cases, the remote desktop protocol will be used, especially for security with just one password. RDP allows you to share and control a computer or desktop remotely. Companies can use it to fall back on an inexpensive and simple way to enable employees to work remotely. A user name and password are required to connect to an RDP server.
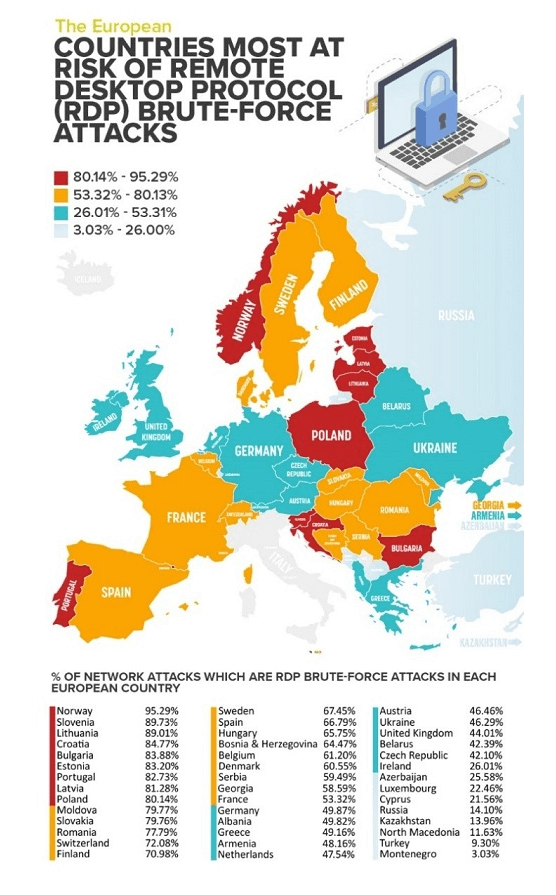
Interested in the prevalence of RDP brute-force attacks, Reboot Online analysed the latest data from anti-virus specialists Kaspersky to discover which European countries are most at risk.
Secure RDP Connections
Companies should minimize the risks of increased use of remote access or similar services. Ideally, RDP access online should be disabled. If this is not possible, experts recommend limiting the number of users who can connect to the company’s servers online. Companies should only allow strong passwords for all accounts that use RDP. They have to use additional verification by means of two factor authentication. Isolate any insecure computers that require RDP access and replace them as soon as possible.
