Hackers are now making use of new java ransomware called the “tycoon” to lock down the files of Linux and Windows users. As we know, hackers are always coming up with new ways to hack the data centers of users and steal valuable information and data.
They majorly attack windows Os because most people use it while still devising, attacking other os like Linux and Max
The Tycoon Ransomware
The tycoon ransomware has been in operation as of 2019. It was name Tycoon by some security experts.
The ransomware is written with java programming language, which enables it to it infect all Windows and Linux users equally.
The tycoon hidden in a Zip file which activates the trojan once the target opens it. The hackers make use of vulnerable servers and the RDP server too to launch their attack.
Once they have run the ransomware on the target’s system, it will begin to gain leverage on the system, and will later cause the IFEO to inject the Windows keyboard to function on-screen.
It will also change the password of the Active Directory and disable the antivirus before installing process hacker as a utility tool.
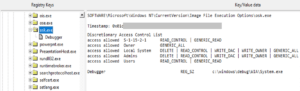
Once it’s done, the ransomware will start encrypting all the data on the computer and the hard drive.
The files that get encrypted with the Tycoon ransomware end up with two extensions, that were not seen so far, “.grinch and .thanos.”
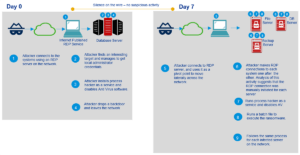
It will then send the private key to the hacker who will then destroy the target’s private key from his system. After all this, it will display the message to the target. The tycoon ransomware is usually used to target small and medium-sized businesses, software companies, and educational institutions to gain large amounts of money from the victim as ransom.
Protection and mitigation
Having a backup of your most important files is one of the ways to protect yourself from the tycoon malware. Make sure that your operating system and all other installed programs are always up to date. Aside from all this, install a good antivirus that is good for the Os that you are using. Also, be careful of the files you download from the Internet. Most of those files may contain malware.
Some file extensions that are mostly used by hackers are redrum, thanos, and grinch while the file signature could be redrum3_0 and happyny3.1.
