Private data of the largest free web hosting provider for dark web services, Daniel Hosting (DH), were leaked by a hacker today.
This doesn’t come as a surprise as the hosting site has been hit severally by hackers over the years. The first attack occurred in November 2018 when the system was hacked and a large number of files were deleted.
Second time DH was Hacked
The second attack took place on the 10th of March, 2020. This led to the permanent shut down of DH services and affected at least 7,600 websites, which comprise at least one-third of dark web portals.
As far as hosting providers go, DH is not the first to be breached. A web hosting provider- Freedom II, that was sheltering the child abuse portal, was also hacked by KingNull; who claims to be a part of the Anonymous hacker collective.
Sensitive Data leaked online
Things seem to be taking nose-dive for DH system as a hacker by the name KingNull uploaded stolen DH data on a file-hosting portal. The data, analyzed by a threat intelligence firm, Under the Breach, contains 7,205 account passwords, 3,671 email addresses, and 8,580 private keys for .onion (dark web) domains.
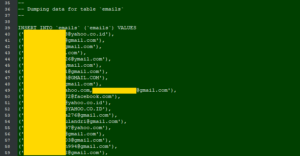
ZDnet was given priority alert about the recent breach due to its history with DH. Under the Breach told Reporters, “the leaked database contains sensitive information on owners and users of several thousand darknet Domains. This information could substantially help law enforcement track the individuals running; or taking part in illegal activities on these darknet sites.”
The agency has warned that if users continue with their old passwords, notwithstanding the hosting web, hackers could still gain access to their accounts.
The leaked data is a proverbial double-edged sword. On the positive side, it could help cybersecurity agencies flush out threat actors that hosted cybercrime-related websites on the darkweb. On the negative side, it could be dreadful for those running political sites; especially if they failed to take the necessary precautions to protect their identities.
Regrettably, IP addresses, which would have been an added advantage for the enforcement, were not included in the leaked data.
