Even those who are not concerned with the security have mostly heard of Emotet. The malware has been up to mischief for several years, sometimes as a Trojan, then as a data thief or quite differently, because Emotet repeatedly loads new malware onto affected networks when necessary.
When it comes to dissemination, Emotet also takes unusual approaches: Mostly it comes with spam mails or uses files for dissemination. But it also tries to crack WLANs within range of affected networks. The people behind Emotet try out a lot, currently the system is posing in spams as an update. Anyone who opens the file attachment with the extension falls into the trap. So watch out for emails telling you to update the applications.
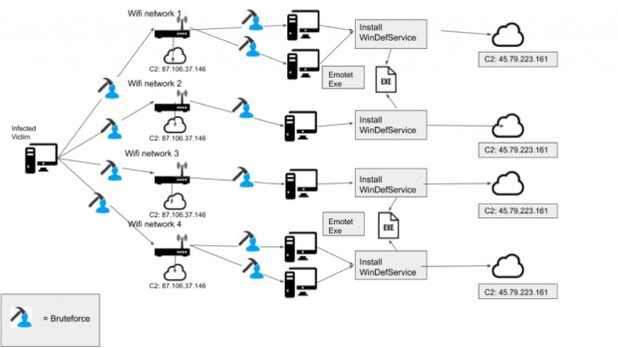
Once you have it on the network, it reloads various types of malware against which nothing is safe. But there are exceptions: With small protection, you can check your network and new tools check whether Emotet is misusing your email or not. A scanner is also required to protect yourself.
A Good Scanner Should Actually Prevent The Malware
Small tools also check whether a system is already hacked with the malware. In the current version, the developers have explicitly added support for the version of the Trojan, which probably started back in April. Suspicious files and attachments can be easily scanned.
The Dangerous Thing About Emotet Is Its Flexibility
Emotet uses a wide variety of ways to hack systems. Since the malware is very clever and uses harvesting to forge emails from users, it has given a high rate on the warning list for a long time.
The malware continues with the distribution in the network. But now researches show that it also scans the available neighboring WLANs on affected networks and then tries to connect to the other ones.
