Hui Peng and Mathias Payer, researchers from Padue University, and Swiss Federal Institute of Technology, Lausanne, respectively, have discovered at least 26 vulnerabilities in the operating system of Linux, macOS, FreeBSD, and Windows.
These vulnerabilities were exposed using a new tool they referred to as the USBFuzz alias known as a fuzzer.
With the fuzzer application, security researchers can analyze a large quantity of unexpected data that are input into the program and monitor how the software behaves to discover new bugs.
The USBfuzz designed with the sole aim of testing the USB driver stack of operating systems.
The researchers, Peng and Mathias, said; “at its core, USBFuzz uses a software-emulated USB device to provide random device data to drivers (when they perform IO operations). As the emulated USB device works at the device level, porting it to other platforms is straight-forward.”
They tested the fuzzer on nine versions of Linux, the latest release of FreeBSD and MacOs 10.15 Catalina, and versions 8 and 10 of Windows.
The results from the test revealed the presence of 26 bugs. The Linux system had a greater composition of bugs, 18 in total. Of the 18 bugs found, two bugs resided in the USB camera driver and Linux USB host controller driver. At the same time, the other 16 were memory bugs located in the high-security impact in various Linux subsystems.
The research then said, “the bugs were reported to the Linux kernel team along with proposed patches to reduce the burden on the kernel developers when fixing the reported vulnerabilities. Of the 18 Linux bugs, 11 received a patch since their initial reports last year. 10 of these 11 bugs also received a CVE, a unique code assigned to major security flaws.
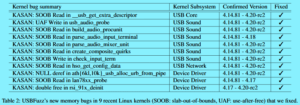
The remaining bugs fall into two classes; those still under embargo/being disclosed and those that were concurrently found and reported by other researchers.”
This isn’t the first time a fuzz test is carried out. In November 2017, A Google engineer used a Google-made fuzzer, syzkaller to discover 79 bugs impacting Linux kernel USB drivers.
USBFUZZ TO BE OPEN SOURCED
Payer released a draft of the research which describes the work of the USBfuzz. This research will be submitted at the Usenix Security Symposium virtual security conference, scheduled for August 2020. Following this talk, the USBfuzz will be released on GitHub as an open-source project.
Peng and Payer re-ascertained superiority of the USBfuzz to other fuzzs like the vUSBf, syzkaller, and usb-fuzzer. Not only does the USBfuzz grant more control to testers it also has general portability across operating systems unlike others that only work on NIX systems
