Security companies foiled an advanced APT led cyber espionage campaign in China to infiltrate a government agency and two companies.
Antivirus companies have uncovered and thwarted advanced cyber-espionage activities against government agencies and two telecom and natural gas companies.The complexity of the attack and the nature of the target indicates that persistent threats from China may be involved. Specifically with a focus on cyber espionage in Central Asia.
The attackers used various previously unknown basic malware and back doors during the attack. Analysis of your code indicates that it may link to various activities discovered in recent years.
Provider Choopa, LLC host most of the C2 the attackers use. Threats used a large amount of Gh0st RAT. The malware was attributed to the Chinese-linked Internet spy organization.
Security companies ESET and Avast detected attacks for the first time since September and January, respectively. Investigators identified a host used as a repository for hacking tools and back doors.
Their code bears many similarities to malware previously associated with APT organizations related to China.
“The samples we analyzed contained links to samples and malware activities, such as Microcin, BYEBY, and Vicious Panda, which were previously described by Kaspersky, Palo Alto Networks, and Check Point, respectively.
As far as we know, the back door discovery is a custom tool that has never been through review before. “Read the report released by Avast.” Most of C & C’s servers register with Choopa, LLC, a hosting platform that has been used by cybercriminals in the past.”
Timeline of attacks that appeared to be associated with the same threat actor
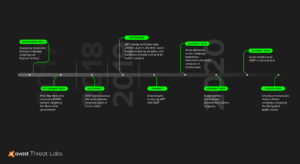
“We believe that APT team from China may have buried the back door for long-term access to the corporate network. From our analysis, we suspect that the organization is still behind the active attacks in Mongolia, Russia, and Belarus,” he continued. Avast.
ESET investigators investigated the attacks and discovered three back doors, collectively called Microceen.
Backdoor programs allow threat participants to manage the target file system, set remote shells, take screenshots, manage services and processes, and execute console commands.
