In a leaked document reveals that a subsidiary of the Avast antivirus manufacturer sold user data collected from its software to customers.
The Mozilla developers had blocked the add-ons from the antivirus providers Avast in Firefox or removed them from the store. The possible reason: The add-ons from this provider have probably passed on private data. The addons are back, but the info got stuck. Then there was evidence that Avast was breaking HTTPS connections and analyzing the content. And there was evidence of cyberattacks at Avast and malware infection at CCleaner. Anyone looking for Avast on the blog will encounter many articles on bankruptcies, bad luck and breakdowns.
A subsidiary of the manufacturer of an anti-virus program, which is used on hundreds of millions of systems, sells highly sensitive browser data of its users to third parties. Buyers include many of the largest companies in the world, such as Home Depot, Google, Microsoft and Pepsi. This was revealed by a joint investigation by the motherboard and PCMag. The report relies on leaked user data, contracts and other corporate documents, which show that the sale of this data is both highly sensitive and is said to remain confidential in many cases between the company that sells the data and the customers who buy it.
Avast Products Collect Data
The documents, which come from the subsidiary Jumpshot of the anti-virus provider Avast, shed new light on the provider’s secret sales and supply chains. The documents show that Avast’s installed antivirus program collects data about user surfing behavior. The documents also show that Jumpshot maintains this data in various products and then sells it to companies worldwide. Some customers have paid millions for products that contain an all clicks feed. This can track user behavior, clicks and movements on the websites with high accuracy.
Complete Online Activities Recorded
The data viewed by PCMag includes Google searches, LinkedIn pages, certain YouTube videos. The data collected can be used to determine the date and time at which the anonymized user visited the sites and in some cases, the search term he entered on the page and the specific video he viewed.
Data Was Collected For Years In Stealth Mode
Avast initially managed the data collection via various browser extensions that were installed during the installation via a plugin. The extensions to the sister product AVG are said to have been used. After this type of data collection was made public by the developer in October 2019, Mozilla and Google removed the corresponding extensions from their respective extension stores. At this point, the data collection could have been running for years, as can be interpreted from the news.
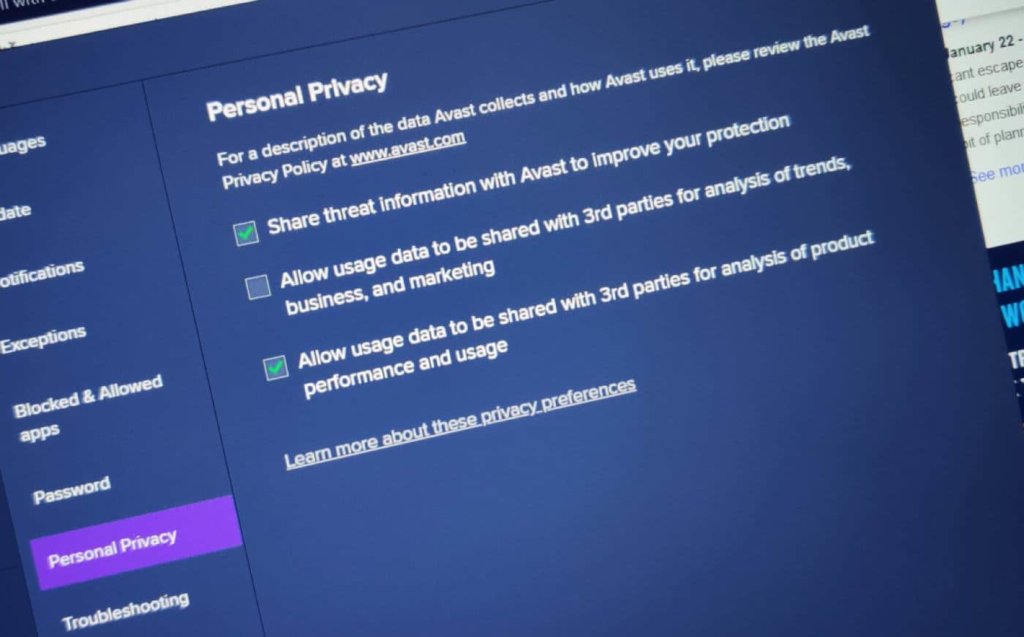
After the disclosure of the activities and the resulting store exclusion, Avast is said to have sent no further data to Jumpshot from any extensions still installed. Instead, the company is now using the antivirus software itself for data collection after the vice investigation.
For about a week now, the software has been asking at least some users for their consent to the data collection. Apparently, the users contacted in this way, do not even think that the consent could lead to the sale of their data to third parties. At least the manufacturer experienced this when asked by users who had already interacted with the pop-up.
Data Collection Should Continue
However, according to the PCMag report, data collection is still ongoing. This is concluded from information from the source and from existing documents. Instead of collecting information about software connected to the browser, Avast is now doing this through the antivirus software itself. A few days ago, months after it was discovered that it was sending data to Jumpshot with its browser extensions, Avast started asking its existing consumers of the free antivirus software to choose to collect data, according to an internal document. Anyone who agreed to this was tracked afterwards.
Sounds like the fans who bet on the antivirus manufacturer thought they were protected from threats. Because at the end of the day they were pretty much pulled over the table and dates. Although the data does not contain personal information such as the names of the users, since they have a wealth of specific browser data. The data are formally anonymized. How apps legally spy on us already indicated that this data can also be deanonymized. PC-Mag points out that the data records are provided with a device ID. Together with the date and the data that can be assigned to this ID, the identity of a user can be revealed.
