Elexon, a U.K. electricity grid network reseller, recently said cyberattacks hit it.
Elexon, a British electricity broker, was the victim of a cyber attack. Therefore, the event affected the internal computer network, including the company’s mail server and employees’ laptops.
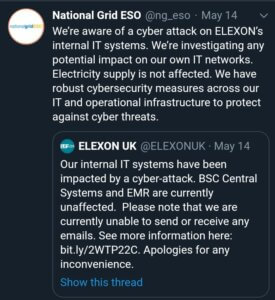
“Hackers target a critical part of the U.K. energy system by keeping people from their systems and preventing them from sending or receiving email.” reads a post from The Telegraph.
“Elexon, a key player in the energy market among power plant operators and home and business utilities. Said in a statement, “that its internal systems and laptops were affected by a cyber attack. It declined to provide further details“.
The company manages electricity the supply and demand therefore, distributes energy over the grid when needed.
“We would like to inform you that ELEXON’s internal computer systems were exposed to a cyber attack today. The central BSC and EMR systems are currently not affected and are working normally. The attack only affects our internal computer systems and laptops.” reads a post from the company’s website.”We are currently working hard to solve this problem. Please note, however, that we are currently unable to send or receive emails.”
The company’s response
The company removed the mail server in response to the attack.
According to Elexon, the systems for managing electricity transit in the U.K. did not suffer any effect.
However, the company released a second message to announce that it has discovered the root cause of the incident.
It noted it is working to fix the internal network of employees’ laptops.
Elexon added that the attack did not affect central BSC systems and EMR and will continue to function normally.
Even though the company did not reveal details of the attack, experts suggest ransomware involvement.
The NSA also warned that several government-sponsored cyberespionage groups are exploiting corporate VPN vulnerabilities.
In January, the U.S. Cybersecurity and Infrastructure Security Agency warns organizations that attackers are exploiting the Pulse Secure VPN vulnerability.
Although Pulse Secure fixed the flaw in April, thousands of Pulse Secure VPN endpoints still need to be fixed. Also, in January 2020, Bad Packets reported that 3,623 vulnerable servers were still present in the Pulse Secure VPN, including 1233 in the United States.
The U.K’s National Grid Agency publicly announced that the incident did not affect electricity supply across the nation