Attackers could attack Android devices through the vulnerability named StrandHogg 2.0 and gain control over many functions such as the camera. However, attacks are not easily possible.
Google Released Security Updates For Its Devices On Patchday
Android partners are said to have received the patch in April. All Android versions up to 9.0 are threatened. The current Android edition is not affected. Root access should not be required for successful attacks.In theory, attackers could basically hijack most legitimate apps from Google Play, for example to get personal information. This can be classified as critical.
For an attack to be successful, a malicious app must already be installed on a vulnerable Android device. It looks like the attacker needs victims to help them set foot in systems.If the requirement is met, attackers could hijack legitimate apps via their malicious code app. If a victim opens the attacked Facebook app using the original icon, the victim runs unnoticed in the background.
Because of the vulnerability, attackers could join in the Android task management function. They could then inject malicious code into newly created tasks, in which the code of the legitimate app is located in parallel. As a result, the task runs with the rights of the legitimate app, but the malicious code works in the background.
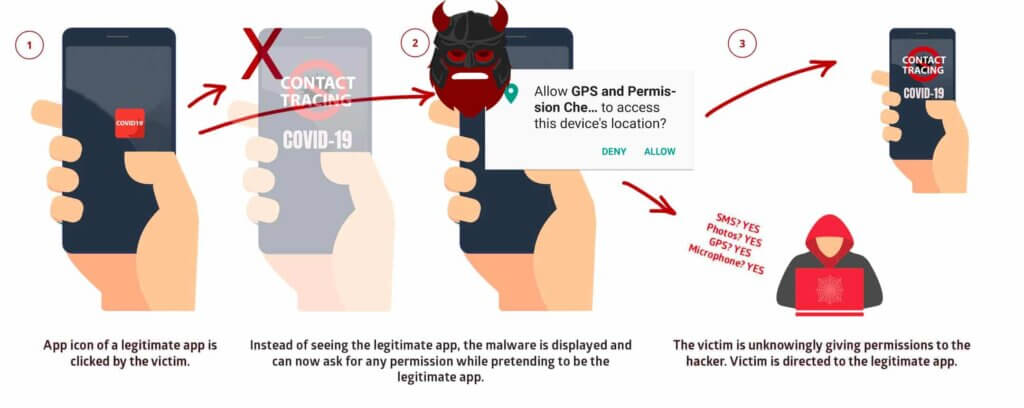
The security researchers provide further details on the attack in a report offered on a website on the vulnerability.The security researchers discovered a similar attack last year. The bug called StrandHogg can be found in the multitasking system of Android. As the name suggests, StrandHogg 2.0 is the improved successor. Attackers can now attack several apps simultaneously. In addition, the further developed malware should work more concealed and leave less traces. As a result, antivirus software has a harder time getting in between.
