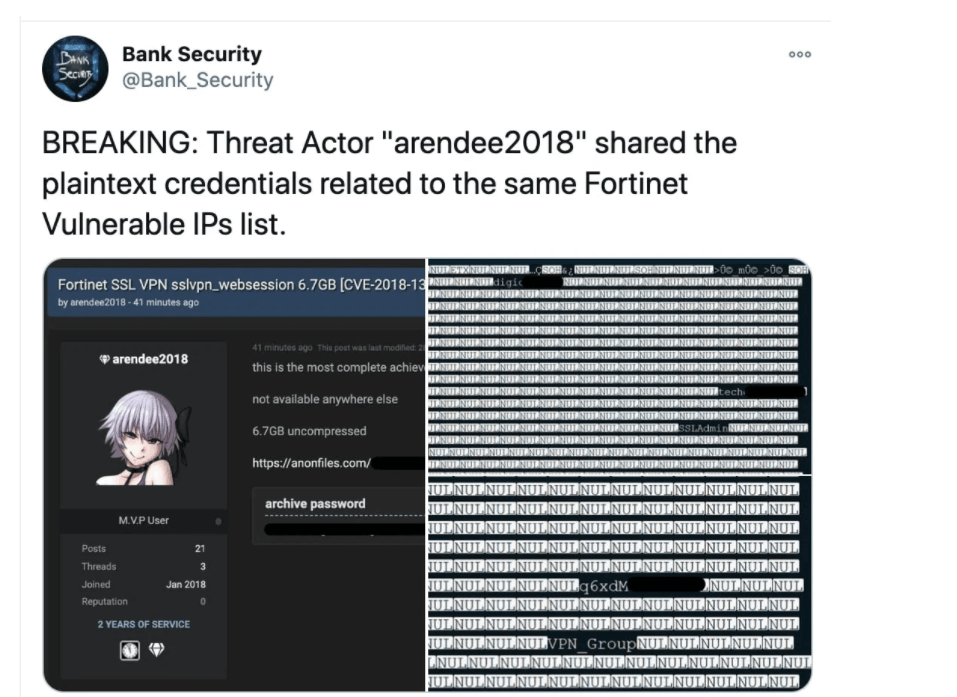
Administrators should change the access for Fortinet VPNs in use. Log-in information for almost 50,000 VPN networks has appeared in various cyber blogs.
A security researcher texted on Twitter that the file should be almost 7 GB in size and partly contain log-in data. The researcher already warned that a report of vulnerable Fortinet VPNs was published. Now the associated access has appeared. Users can also see the access rights.
Patching Alone Is Not Enough
By successfully exploiting the vulnerability, hackers could access the files that were actually stored. There you will find, among other things, unencrypted user names and log-in data.Patches have been available for around two years. The issue is, because of the leaked access, even VPNs that have been secured in the meantime are at trouble until administrators exchange the log-in. This should also happen for all online providers that use similar log-in data.If that doesn’t happen, the hackers could launch identity attacks on VPNs and try out whether entries from the work and grant them access. According to the security researchers, most of the affected IP locations belong to US government pages.
Sending prepared requests should be sufficient for a successful attack on which the VPNs are based. If this works, hackers could access the files and thus gain access to unencrypted access. They could then log into vulnerable VPN networks and compromise them.Attacks on the security gap are already taking place. In October it became known that hackers had broken into US government systems through the vulnerability. Fortninet collects the saved options in a warning text.
Therefore, it is strongly recommended that all administrators and security experts resolve this serious vulnerability immediately. Also, users should change their log-in immediately, both on VP devices and on other pages that share the same access data.
