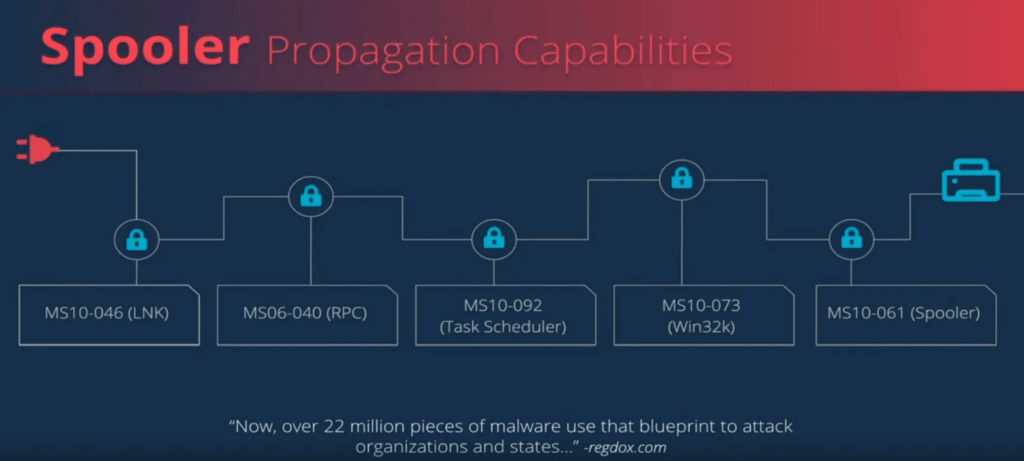
The computer virus Stuxnet successfully attacked control systems of industrial plants for many years. In order to infiltrate the system control, it took the detour via connected Windows systems and used an exploit chain of remote code execution and subsequent local privilege expansion.
Researchers investigated the question of whether a Stuxnet 2.0 scenario would be conceivable, despite the long-term bug fixes. In a presentation at Black Hat 2020, they explained and showed why this question can be answered with a clear yes in their opinion. The researchers paid particular attention to the last link in the exploit chain – the Windows printer spooler, which Stuxnet used at the time for the final jump to the systems. In the process, they discovered two new vulnerabilities that they reported to Microsoft. One of the vulnerabilities CVE-2020-1048 is expected to be closed this month. The other did not find Microsoft relevant enough to close it.
Old Exploit Chain Remains Dangerous
Using Stuxnet’s original exploit chain, the researchers explained in the lecture how Microsoft closed the gaps at the time. Above all, they criticized very special placed fixes – narrow patches, which can sometimes be canceled out by modifying the original attack slightly. Alternatively, it is also easily possible to replace old gaps with equivalent gateways.As the researchers explained, the original Stuxnet strategy and its obvious reactivability is still highly relevant and problematic today, as it is still used over and over as a draft for a wide variety of malware campaigns.
The Second Security Problem
The second security problem discovered by the researchers is more than 20 years old and affects 32 and 64-bit Windows releases from version 2000. They discovered it through so called fuzzing, a variant of automated tests, within around 15 minutes. The bug can be exploited locally and could be misused by a local attacker to provoke a printer spooler crash. However, Microsoft does not classify the resulting risk as high enough to publish an update.
