Security researchers of Bluetooth describe gaps in the authentication process of the classic Bluetooth devices that allow a third party device to connect to a nearby device.
The crux of the matter is the so called pairing when establishing a connection between Bluetooth device. So that a user does not always have to confirm a connection between a smartphone and headphones, a long-term secret key is agreed upon the first connection. This is then sufficient for future connections.
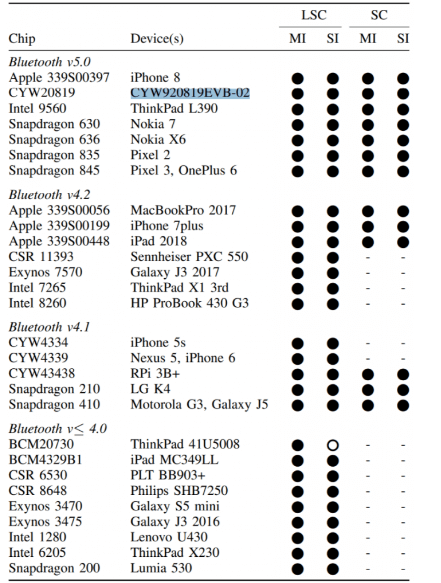
The researchers have now succeeded in faking a Bluetooth device into the identity of another device that has already been paired, and thus establishing a connection. Before that, an attacker can create a pairing process between two devices and thus learn public information such as the Bluetooth name, addresses, protocol version numbers and capabilities. Here’s the list of the devices tested:
The Discoverers Call The Attack Method BIAS (Bluetooth Impersonation Attacks)
Numerous Bluetooth devices and chips are affected because the problem is due to the classic Bluetooth protocol, which practically all devices such as smartphones, tablets and laptops use. The security experts successfully carried out the attack on Bluetooth devices, including iPhone, various notebooks and pixel smartphones.
The problem was discovered and reported to the Bluetooth Special Internest Group at the end of last year. The group then adapted the Bluetooth core specification. However, firmware updates for the Bluetooth chips are now required. So far, the researchers have not been able to say whether these have already occurred. Apple has not yet released more information on patched security holes for the iOS update.
To what extent the security vulnerability demonstrated is really being used in practice is unclear. Attacks do not work worldwide, but only within the reception range of Bluetooth devices, which is usually close to 10 meters with a clear view. If you want to protect yourself better, you should switch off Bluetooth when you don’t need it.
