Whether in the automotive industry, in mechanical and plant engineering or in the consumer goods sector – digitization does not stop at any industry. This also applies to the core of every company’s value creation: its intellectual property. To the extent that digitization of intellectual property helps, Cynet exposes fewer risks such as loss or theft. In theory, there is no danger of showing the attacks and scandals: 100% security is an illusion in the digital world. And that is exactly why IT security is not just a technical problem. Rather, it should be viewed and treated as part of the company’s risk management. In addition to technology, people and processes must also be included. IT security providers and analyst firms have more and more solutions and concepts for threat analysis or elucidation in their offers and statements on the development and supplementation of threat protection – all assuming that attacks are successful.
This Is How Companies Recognize An Offender From Inside
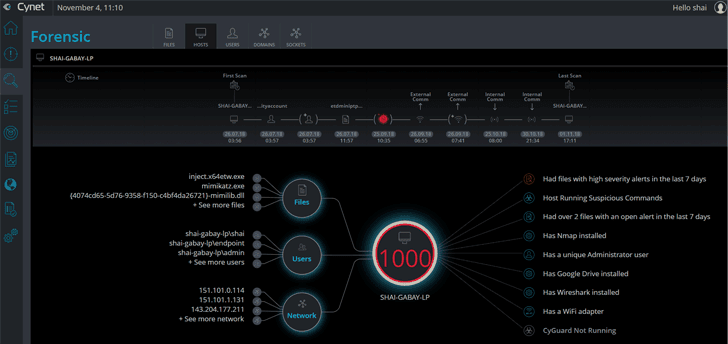
The discussion about Cynet IT security focuses in particular on external attacks. According to estimates by the Federal Office for the Protection of the Constitution, the cyber actually occurs much less frequently than attacks from the company itself: The office speaks of a ratio between internal and external attacks. Experts from various security companies come to a similar assessment. The discussion about IT security in companies by no means reflects the actual threat situation. But how can a company realistically assess the risks posed by internal criminals? How do you recognize an inside job – especially against the background of labor law, which only allows workers to be monitored to a very limited extent? One answer is: You can recognize the risk of an attack from the inside by suspicious behavior, more precisely by deviations in behavior from the previous, unobtrusive behavior of an employee.
Threat Analysis Predict Hazards
For this reason, behavioral analyzes should not shed light on the individual event, but rather patterns and relationships that arise from the behavior of the user. In this way, risks or threats can be directly assigned to specific users, projects and periods. The information is always and immediately available, so that effort and costs are significantly reduced compared to classic forensic projects. Versioning solutions to manage intellectual property are the source of this information. This necessarily results in meta data that can serve as the perfect basis for behavioral analysis.
