The experts at G Data CyberDefense counted more than 4 million malicious apps. New Android malware applications appear every day. The focus is on adware to tap personal data and resell it.
Adware Is Currently Experiencing A Real Renaissance
It is being used increasingly on mobile devices in particular. Even if it does less damage than ransomware at first glance, adware should not be underestimated. Because these malicious apps also collect personal data such as locations or read the browser history. Data that malware authors use to make money.
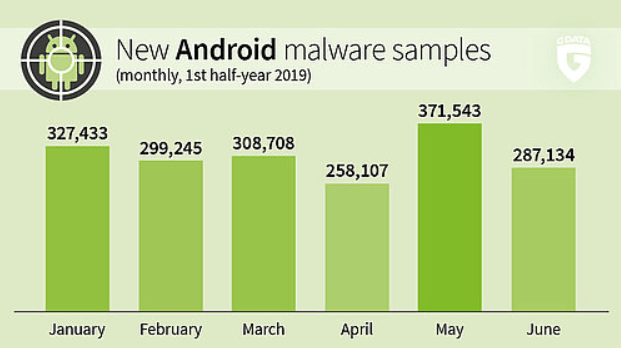
The sharp increase is also due to the fact that developers continue to develop their adware technically. For example, they circumvent antivirus programs or operating system restrictions. Unlike malicious malware such as ransomware, no elaborate techniques are required to develop appropriate adware apps. The effort is minimal, the yield is maximum. As a rule, these advertising slings get into the system involuntarily with a downloaded app and constantly display unwanted advertising. Free apps in particular often contain adware as an alternative source of income.
Android malware attacks on devices are currently mainly aimed at private individuals and less at companies. Although manufacturers of mobile devices are paying much more attention to security, the number of malicious apps is increasing. Adware is particularly common on smartphones and tablets.
Minimal Effort, Maximum Yield
According to the security provider, adware is currently experiencing a real renaissance. It is being used increasingly on mobile devices in particular. Even if in contrast to extortionate ransomware, it does less damage at first glance. Adware should not be underestimated, the company says. Because the malicious apps also collect personal data such as locations or the browser history.
